Test Altospam’s solutions!
Thousands of companies, CTOs, CIOs, CISOs and IT managers already trust us to protect their e-mail against phishing, spear phishing, ransomware, …
Ransomware is a ‘virus’ whose aim is to hold your data hostage in exchange for a ransom. Ransomware is most often propagated by email in the form of an executable in an attachment. If you are unlucky enough to run this program, it will infect your computer and spread across the local network. Very quickly, all important files on the infected computer will be encrypted, making them unusable. You’ll have to pay a ransom to the ‘pirates’ to get your data back, but nothing is guaranteed…
The phenomenon is not new: ransomware has been around since 1989. There are all kinds, and the principle is to extract money in exchange for access to your own computer or data! Some of them, like “Reveton”, also pretend to be government authorities, like the FBI, and tell you that you have to pay a fine to get your data back… Another form of ransomware is “Winwebsec”, a fake antivirus that you can download from a browser window, making you think that your PC is infected.
In recent months, however, ransomware has become increasingly prevalent and, above all, extremely sophisticated. Some of them, including the most dangerous “CryptoLocker” (and its variants) and the “ACCDFISA” family, encrypt data to such an extent that it is currently impossible to decrypt it without the key. CryptoLocker has infected about 234,000 users worldwide, it is considered by CERT US to be very dangerous: http://www.us-cert.gov/ncas/alerts/TA13-309A.
Some versions of ransomware are able to encrypt not only local files, but also stored files, USB sticks, external hard drives and shared files. Outsourced backups can also be compromised if they perfectly synchronize local data, so it’s important to use a backup that incorporates versioning [Cf. Tip 1].
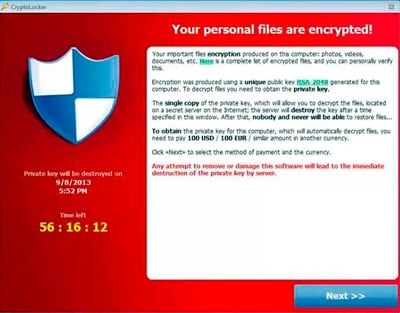
To encrypt your files, CryptoLocker generates a 2048-bit RSA biclef. The private key is sent to the hacker’s server for later decryption, while the public key is used to encrypt photos, videos and documents on your hard drive and on drives shared directly as external drives. Encryption is performed using the AES-256 algorithm, ensuring a perfect seal against brute-force decryption. After encrypting the data, CryptoLocker gives you 72 to 100 hours to send the ransom (usually around $300), after which the amount will be significantly increased (*10 approx).
Although dismantled in early June 2014 by the FBI, the “Gameover Zeus” botnet, which used P2P technology to build a botnet of zombie computers and served as a base for the propagation of the CryptoLocker malware, has just been reborn using the so-called “fast-flux hosting” technique under the name: “Try Again Zeus” : http://blog.emsisoft.com/2014/07/11/gameover-zeus-decides-to-try-again/.
On the other hand, imitations such as “CryptoLocker 2.0”, “CryptoDefense”, “CryptoWall” and “CryptorBit” are also very dangerous and still active. The architecture, means of propagation, languages used and/or encryption methods differ slightly from one program to another, but the general principle remains the same. Some ransomware had imperfections that allowed decryption, but these were quickly corrected.
You can find out more about CryptoLocker at: http: //www.bleepingcomputer.com/virus-removal/cryptolocker-ransomware-information
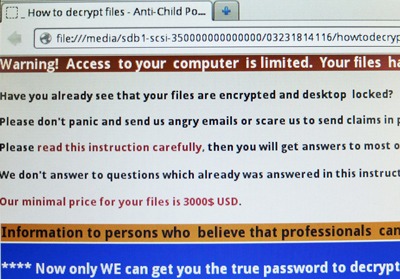
Unlike most malware, “Anti-child Porn Spam Protection 2.0” does not use phishing attacks to spread and infect the target system. This malware is propagated via the RDP [Cf. Tip 4Most often detected through “wildcatting” of your IPs and brute-force attacks via the RDP remote access protocol with specific, commonly used accounts such as: 123, adm, admin, Administrator, backup, Guest, scanner, support, test, user, … or through a security hole in the remote system […].Cf. Tip 3].
In the case of “Anti-child Porn Spam Protection 2.0”, files are encrypted in AES-128 using a customized version of WinRAR compression software in self-extracting mode. Data is first encrypted using a symmetrical key combining a randomly generated 50-character string and a static string. The random string is temporarily stored in a local file, sent to the hackers’ server for decryption and finally deleted using a built-in ‘shredder’ routine, making recovery of the original file impossible. After this initial encryption phase, a second password of between 80 and 114 characters is generated to encrypt the files a second time. This second key is stored locally and may eventually enable decryption, but recovery of the first key is virtually impossible.
The hackers behind this ransomware are asking for between $3000 and $4000 minimum, clearly stating that it will never be less, even if you only need a single file.
For more information on the ACCDFISA family of ransomware, visit: http: //blog.emsisoft.com/2012/04/11/the-accdfisa-malware-family-ransomware-targetting-windows-servers/
Now that we’ve highlighted the disasters that this type of ‘virus’ can cause, here are a few tips on how to avoid paying the price. Since most malware arrives via e-mail, the ideal solution is not to receive the infected message at all. That’s why it’s so important to have a good antivirus program upstream, capable of detecting viruses embedded in attached files [Cf. Tip 2… but also on your workstation to avoid contamination by other means. But as no system is infallible, the most important thing is to have a backup, so this tops our list of tips. The population concerned is shown in square brackets.
Tip 1:[Administrator] Use a backup service that supports versioning, preferably outsourced, to limit the risk of malware propagation over the network. It’s important to be able to go back to older versions of a file.
Tip 2 :[Administrator] Install a good anti-virus software, with regular updates, if possible upstream of your mail server. By way of example, ALTOSPAM integrates 5 antivirus programs as standard, and automatically checks suspicious attachments with its partner VirusTotal, guaranteeing its customers top-level protection against ransomware. Details at: https://www.altospam.com/actualite/2014/02/la-forteresse-daltospam-les-malwares/
It seems that some versions of ransomware are also sent by e-mail in “encrypted ZIP” attachments, for which the correspondent will give you the password in the body of the e-mail. In this case, antivirus software can’t do its job, so be extra vigilant!
Tip 3:[Administrator] Keep your system and applications up to date. Security updates must be applied to operating systems as soon as possible. Some ransomware exploits Microsoft vulnerabilities, for example.
Tip 4:[Administrator] Avoid unnecessary remote access. RDP (Remote Desktop Protocol), used in particular by “Anti-child Porn Spam Protection 2.0”, is a protocol that allows a user to connect remotely to a computer. The default port is TCP/3389. If an account is compromised, access to your network will be easy.
– Access should not be possible from the Internet, if it is necessary to change the default port and/or restrict access to specific IPs,
– check which accounts have access rights to the remote desktop and keep only those that are really useful – not everyone needs this access. Delete all unnecessary accounts, such as “guest”, “test”, “user”, …
– all user passwords must be sufficiently strong (with upper and lower case letters, digits and signs, and at least 12 characters long), especially for accounts with remote access rights.
Tip 5:[Administrator] Make your users aware of security issues and this type of risk, in particular by communicating the tips below, preceded by the word[Users].
Tip 6:[Users] Be careful with links in emails, don’t click them unexpectedly. Always check, for example, that the written URL corresponds to the redirection address and that the site is spelled correctly.
Tip 7:[Users] Be very vigilant and suspicious of attachments, including those from known contacts (who may have had their account hacked). Be very careful with ZIP files in e-mails; test the archive with an online multi-scanner such as http://www.virustotal.com (Altospam’s built-in automatic scanner).
Tip 8:[Users] To prevent abuse of file extensions, we recommend that you configure your file explorer to systematically display file extensions. To do this, in your file explorer, click on : Organize / Folder options / View / Uncheck: Hides file extensions of known types.
Above all, don’t pay the ransom, for several reasons: on the one hand, you should never give in to blackmail and, despite the ransom, there is obviously no guarantee of recovering your data once you’ve paid it. According to the forums, some users have confirmed that they paid without receiving the decryption key, while others report that not all files could be decrypted.
1. Immediately unplug the network cable and disconnect all networks,
2. File a complaint with an ESCI (Enquêteur Spécialisé sur la Criminalité Informatique) from your local SRPJ (Service Régional de Police Judiciaire),
3. Remove the malware: ask a professional or search the Internet for tools or procedures to remove the virus,
4. Change all your passwords, on your system, your network, but also all your online passwords if possible,
5. Check your entire IT infrastructure, understand how the malware got in, and take the necessary steps to secure your business.
If you decide to give in to the blackmail and pay the ransom, then don’t delete anything, don’t touch anything on the infected PC, and don’t run antivirus software, as this could compromise the decryption process.
If one of these malwares is detected on your computer, but your data has not yet been encrypted, don’t restart your computer. There are tools available to eradicate it, and here’s a list for CryptoLocker: https: //www.us-cert.gov/ncas/alerts/TA14-150A
In conclusion, what is the value of your data? Would your company survive if it lost all its computer data overnight? What can you do to further secure your data and that of your company?
Beware, there is now also ransomware on Android, so even with your phone, be careful!
Test Altospam’s solutions!
Thousands of companies, CTOs, CIOs, CISOs and IT managers already trust us to protect their e-mail against phishing, spear phishing, ransomware, …