Test Altospam’s solutions!
Thousands of companies, CTOs, CIOs, CISOs and IT managers already trust us to protect their e-mail against phishing, spear phishing, ransomware, …
Electronic mail enables the exchange of messages to through a computer network. It predates the advent of the Internet, and is one of its most important building blocks. It has naturally evolved considerably since its creation, uses several protocols and is supported by a large number of RFCs. Always evolving, it continues to inspire research and improvement.
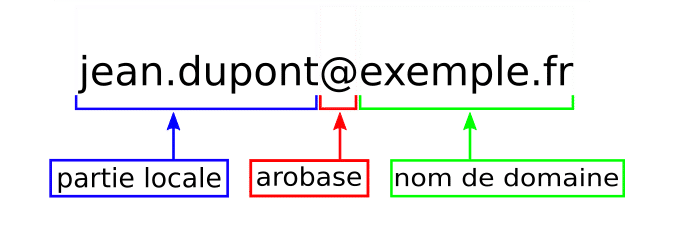
An e-mail address is made up of 3 elements:
– a local part, usually the name or initials of the person using the box.
– the @ symbol, which acts as a separator,
– the fully qualified domain name.
The local part is defined by RFC 3696(https://tools.ietf.org/html/rfc3696#section-3). This one is particularly permissive. In reality, many servers are more restrictive. We therefore advise you to limit special characters to be compatible with as many implementations as possible as possible.
Each domain must include two management addresses: “abuse” and “postmaster”. They are used respectively to collect complaints about abusive behavior, such as spam (see RFC 2142: https: //tools.ietf.org/html/rfc2142#section-2) and technical error messages concerning the domain’s messaging system (see RFC 5312: https: //tools.ietf.org/html/rfc5321#section-4.5.1).
When sending a message, the first thing a sender server does is make an MX (Mail eXchange) DNS query on the “domain name” part of the recipient e-mail address. The purpose of this request is to retrieve the IP address of the domain’s mail server. This step is defined by RFC 2821(https://tools.ietf.org/html/rfc2821#section-5).
It is entirely possible, and even advisable, to have several MX records for a given domain. The MX field priority value. It indicates the contact order of the servers: a connection is attempted to the server with the lowest value. In case of If this fails, we try on the next server and so on. If two servers are designated with the same priority, contact is made randomly on one of the two, thus forming a minimum load distribution.
Finally, this is not a recommended configuration, but it is possible to have no MX record. We then look for a field A (which must return an IP address). If present, a connection is attempted to this address. If no MX or A field is specified for the domain, the shipment fails. An error message is generated by the and sent to the sender.
Note that an MX field must not be an alias (CNAME) such as defined by RFC 2181(https://tools.ietf.org/html/rfc2181#section-10.3) to avoid unnecessary multiplication of requests.
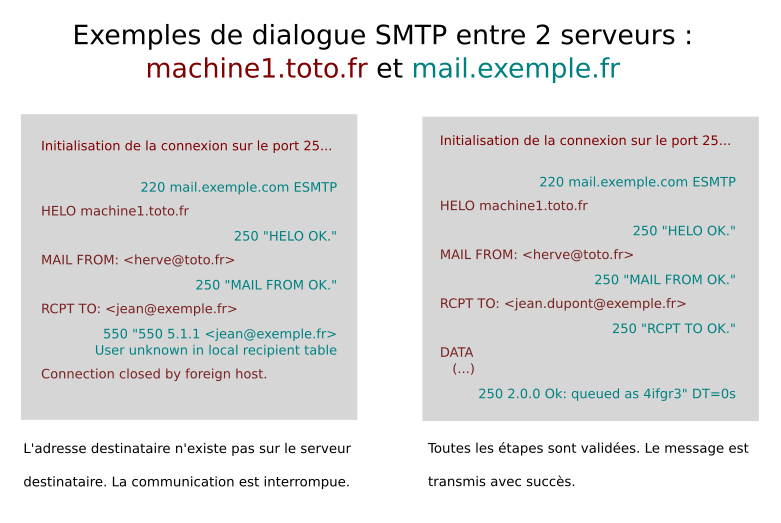
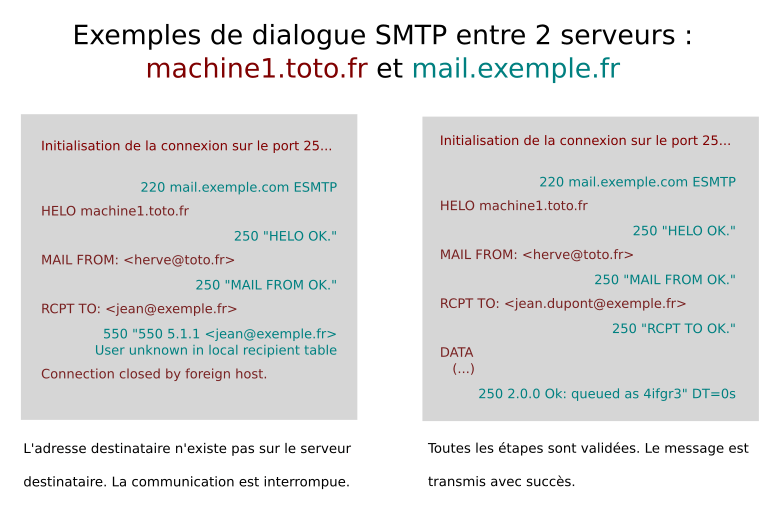
Once the address of the mail server has been established, a connection is initiated by the sending server. This uses the SMTP (Simple Mail Transfer Protocol) protocol on port 25. This communication takes place in four stages:
– HELO (or EHLO): The sending server appears, with its host name.
– MAIL FROM: The sending server indicates which address the message comes from.
– RCPT TO: The sending server indicates the destination address of the message.
– DATA: The content of the message itself, including headers, is transmitted.
A number of other commands exist, but they are optional. This is the case with VRFY and EXPN, for example.
At each of these stages, the destination server must reply that he agrees to continue the conversation. We use a return code :
– 2XX: accepted, we go on to the next step.
– 4XX: temporary block. The connection is terminated and the sending server is prompted to send again at a later date.
– 5XX: permanent lock. Transmitted information triggers an error or rejection on the destination server. Communication is interrupted and will not be renewed.
In the event of a dialogue interruption (temporary or the sending server is prompted to attempt a similar connection on the next mail server, as described above. That’s why It’s important to provide the same level of security for all your mailboxes. A secondary server is considered less crucial and therefore less important. well secured will be an easy entry point for spam attacks in particular.
If the communication cannot be completed, on all available servers, an error message indicating the failure of the is generated by the sending server and transmitted to the sender.
From the outset, the SMTP protocol was designed to transfer plain ASCII text only. It cannot therefore handle rich text (special or accented characters) or binary files. What’s more, these days, most e-mail messages contain an HTML/CSS version that enhances their readability and appearance (integration of links and images, layout, etc.). It was therefore necessary to add methods and standards to the SMTP protocol to enable it to support these formats. This is the role of MIME (Multipurpose Internet Mail Extensions), which is now widely used.
MIME is a standard(RFC 2045 to 2047) that defines mechanisms for transforming any type of data (multimedia files, images, office documents, executables, etc.) into ASCII-coded plain text. To do this, it uses headers that indicate the format of the data contained: the type and encoding used.
This is typically the e-mail client (fat client or webmail) that transforms data into MIME before transmitting it to the server messaging. These data will be extracted (sometimes referred to as “demimed”). by the recipient’s mail client. Nevertheless, it is often necessary for the recipient mail server to extract the files in order to carry out anti-virus or anti-spam checks.
The message is now correctly received by the server but the recipient doesn’t know how to make it available to users. He must pass it on to the MDA (Mail Delivery Agent), which is the mailbox manager, he will be able to store, sort and manage (folders, tags) and make messages accessible to users. The also enables automatic classification according to sender or recipient. headers, for example, including moving to folders “Spam” or “Unwanted”.
The MDA can be contacted via IMAP protocols to access or POP to copy messages to mail clients. The protocol We recommend the more recent IMAP, which can be used to synchronize messages and their organization across all your accesses if you use different terminals.
Some messaging solutions integrate all these services, for example Gmail, Zimbra or Exchange, which can manage the entire chain. Others separate the different services, such as Postfix, which only manages SMTP traffic (MTA, Mail Transfer Agent), or Thunderbird, which only manages mail clients (MUA, Mail User Agent).
In all cases, all 3 bricks are required:
– an MTA for sending and receiving,
– an MDA for storage and access,
– a MUA for reading and writing (the e-mail client).
Altospam is a secure messaging system. Technically, it acts as a relay upstream of the mail server, via the MX fields of the client domain. All messages sent to the domain are therefore directed to Altospam’s servers. They are then extracted (demimed) and checked:
– SMTP validity : The system checks that the sender domain is correctly configured, that the sender server is authorized to transmit for this domain, etc.
– Antivirus control, antimalware: Altospam integrates 6 antivirus programs, each with its own database. data and methods, updated on a regular basis. We are to block a maximum number of known and unknown threats: viruses, malware, ransomware…
– Technologies anti-spam, anti-phishing: We use several anti-spam systems, antiphishing, antiscan, antifovi, whose role is to identify and categorize suspicious messages.
If all checks are passed, the original message is transmitted to the domain’s destination server. The only change made is to add headers validating that the message has been checked(X-ALTOSPAM). The message is completely unchanged, since analyses and controls are made on an extracted copy which is automatically deleted. As soon as the message is transmitted, successfully or unsuccessfully, to the recipient, it is deleted. of our servers. The only time we keep the message is when there is a uncertainty about the treatment to be applied. He is then placed in quarantine for 28 days. It is not delivered, but the user or the administrator of the box concerned can release it.
Finally, if the mail is rejected, no message is sent. to the destination server, saving bandwidth and resources. A daily summary message or the use of the control interface. in charge of informing the user of operations carried out on messages for him.
In all cases, we retain, in accordance with the law, metadata (in the form of logs) for 1 year: date and time, sender and recipient, as well as the message title.
The Altospam system is therefore able to insert itself into the messaging flow of a domain, by in accordance with the protocols governing electronic communications, without impact specific client server configurations.
Test Altospam’s solutions!
Thousands of companies, CTOs, CIOs, CISOs and IT managers already trust us to protect their e-mail against phishing, spear phishing, ransomware, …