Test Altospam’s solutions!
Thousands of companies, CTOs, CIOs, CISOs and IT managers already trust us to protect their e-mail against phishing, spear phishing, ransomware, …

In view of the increasing number of e-mails impersonating senders, or requests to change your e-mail password or validate your personal information, we thought it important to give you a few tips to protect yourself against theft of private data, and above all to avoid FOVI or president scams.
As a reminder, when an e-mail is sent, it is made up of an address that sends the e-mail: this is the address of the e-mail envelope. The same applies to company mail sent by post. the stamp of the company or organization sending you the letter. affixed, but you don’t yet know who the author is. You are informed then the address of the person writing to you. To resume the In comparison with postal letters, the sender is the person who signs the letter. letter.
This is all the more true when the transmitter uses a mass e-mailing system for newsletters or advertising.
If you are anAltospam customer, most of these unsolicited emails will be rejected. The Altospam solution incorporates specific filters to block FOVI or “president scams”.
Let’s take an example to explain this point. We’re not just talking about the technical terms that should be used.
Let’s say you receive an e-mail from Jean-Paul BELMONDO at gmail. You know him and are used to exchanging e-mails with him on a gmail address: jean-paul.belmondo@gmail.com .
In your e-mail program or webmail, the sender of the e-mail will be displayed as “Jean-Paul BELMONDO
Another example: jean-michel-blanc@conservation.fr and jean-michel-blanc@conversation.fr. On first reading, you may not see any difference between the two, but here again, a simple reversal of the letters changes the sender of the e-mail, and the request made via this e-mail becomes illegitimate. This is the principle behind the President’s Scam or FOVI.
As explained at the beginning, the address on the e-mail envelope may be different from the one displayed in your software. This is how spammers make you think they’ve hacked into your e-mail address: they ask you to pay them a fee so they can delete you from their files. When in doubt, never reply to an e-mail that seems suspicious.
The reply-to address, otherwise known as the “Reply-To” is the default email address used by your software or webmail to reply to a message. So to make sure you to reply to your caller, simply click on reply.
Clicking on reply will not send the e-mail, it will only allow you to check whether the address who wrote to you and the one you’re forced to answer. If there is a notable difference, i.e. if the domain is not the same, there is eel under rock. So beware.
The language of the mail is especially valid for all requests for validation of your personal information, password changes, etc. passwords to your mailbox or so-called pending e-mails on your server.
These e-mails should be written in French if you are French. However, most of this type of e-mail is phishing, is in English and always comes from either your domain host or your e-mail host.
In absolute terms, if someone can ask you for this type of information, the e-mail must come from your management or your computer scientist. These people will do it in your language and, above all, in your language. will explain the reasons for these requests for modifications and how to do.
It’s customary to include links to websites or files in e-mails. Without precautions on your part, the worst can happen: you click on a link, a download occurs or a program is launched without your knowledge, you fall victim to a virus or ransomware that blocks all your data on your pc. Beware: malware can spread throughout your company. What’s more, you may be redirected to a site that’s a carbon copy of a site you’re used to logging on to: if you enter your login details, they’ll be stored in the hacker’s or spammer’s database.
Dangerous links are those that actually hide the destination of the link. For example, you might have a link like www.entreprise.com in your e-mail. This link appears to point to the company’s website, but if you move your mouse over it, you’ll see that this isn’t the case at all, that this link is very different and therefore potentially dangerous. In all e-mail programs, when you point to a link, the full address of that link appears in the bar at the bottom of your program.
If this link is too long, you can right-click on it. then copy the link address into an empty text file, so that you can see the whole link.
Here’s an example to illustrate the issues and links in an e-mail :
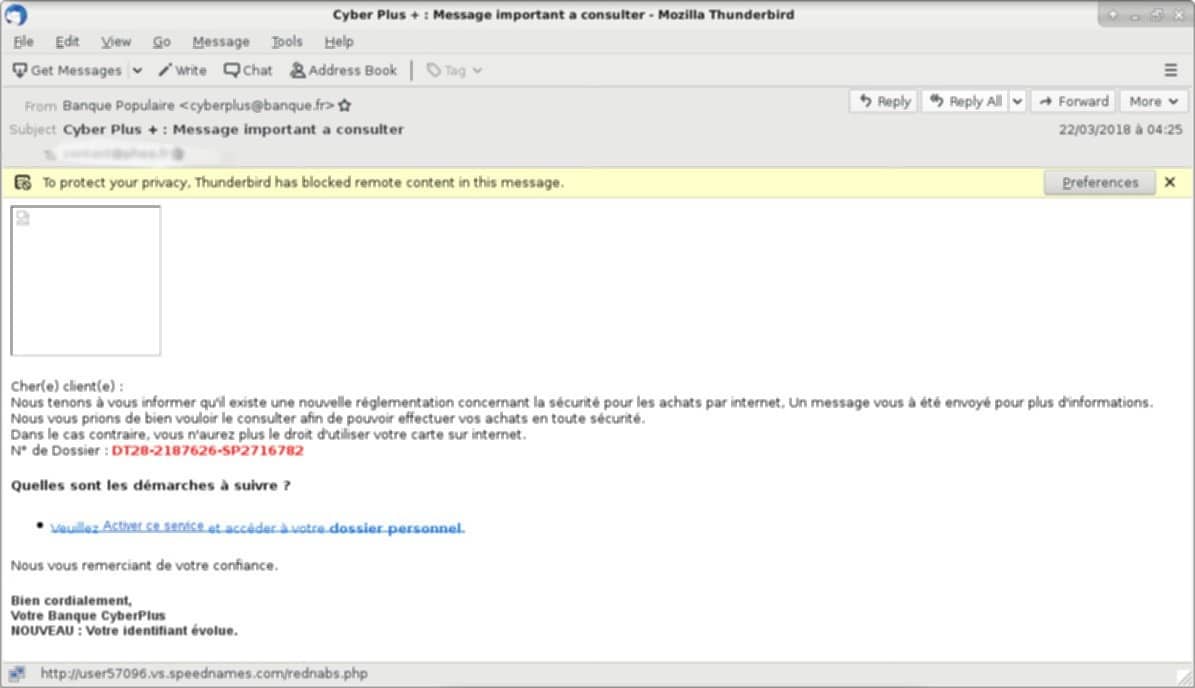
You can see from this screenshot that the sender is posing as the Banque Populaire, that the link to the service does not point at all to the Banque Populaire website. bank.
If you’re in any doubt about the link, you can use online tools such as VirusTotal or MetaDefender from OPSWAT, which will scan this url for you.
Tips for short links like http://bit.ly/58964DsG or http://Goo.gl/48742HjvI45, when you copy it into the url field of the site used, add a + at the end to get the analysis of the genuine link. For the http://tinyurl.com type, add the word “to http:// and tinyurl.com, again to obtain the “preview. true url analysis.
Just because you have anti-virus software on your PC that no virus can infect you. Your anti-virus may not be up to date. day or its antivirus database does not contain this new virus. It’s better lose 2 minutes analyzing a file rather than losing all your data.
Saving an attachment to your PC is not in itself dangerous, but opening or executing it is. Again, you can use VirusTotal or MetaDefender, but also VirSCAN. Just put the file in the file section and it will be scanned by several different antivirus programs. This gives us the widest range of antiviral bases.
On the other hand, for PDFs, it can be useful to transform (via online tools) the PDF into a JPG before opening it, using the pdf2jpg or PdfToImage websites, for example. Turning the file into an image will remove all the hidden and potentially dangerous code inside. Another solution is not to use the usual PDF reader, but a lightweight reader without an integrated script launcher.
To sum up, here are the precautions you should take at when you check your mailbox:
– Always be vigilant when you receive an e-mail,
– Take a few seconds to check the address you’ve chosen. sends the e-mail,
– Analyze the links and attachments contained in the mail,
– If in doubt, contact your IT specialist or your computer support,
– For greater security and peace of mind, protect your professional messaging system with Altospam.
Test Altospam’s solutions!
Thousands of companies, CTOs, CIOs, CISOs and IT managers already trust us to protect their e-mail against phishing, spear phishing, ransomware, …