Mailsafe
Phishing, spam, ransomware, viruses, security starts in your mailbox.



Spamming is a real problem, leading to a drop in employee productivity and a degradation of bandwidth, representing a high cost for companies. The figures speak for themselves: nearly 72% of all e-mails are spam!
To combat this global scourge (the majority of spam comes from outside Europe), French company Altospam has come up with an ingenious solution that combines performance and simplicity. It’s called Mailsafe, and it’s an outsourced online service that takes the hassle out of dealing with spam. This solution saves you from heavy and costly investments, since the fight against spam and other threats (phishing, spear phishing, ransomware, viruses…) is entrusted to professionals who guarantee the quality and availability of the service.
Mailsafe: our anti-phishing, anti-spear phishing, anti-ransomware, anti-spam and anti-virus solution
Altospam’s Mailsafe is a comprehensive service for protecting professional e-mail systems, integrating several levels of security for your e-mails. Built around a comprehensive, high-performance French antispam, Mailsafe provides comprehensive e-mail security. Mailsafe blocks most unwanted e-mails, but above all our anti-spam & anti-phishing solution has been designed to keep false positives to a minimum.
Altospam’s Mailsafe solution is an outsourced anti-spam and anti-virus filter that requires no installation, administration or maintenance, and therefore no human investment. In other words, your company benefits from email filtering techniques without any investment. Your e-mails are processed and analyzed in real time before final delivery to your mail server. Altospam also improves network performance and security by blocking spam and unwanted emails before they even reach your server.
Altospam also fights against lower staff productivity and considerably reduces the legal risks for your company’s manager: using your mail server as a relay, obligation to protect employees against pornographic or offensive e-mails.

Mailsafe features
Anti spam
Altospam’s Mailsafe is located upstream of your mail server. It processes and blocks unsolicited incoming e-mails before they reach your systems. All logs and reception information are accessible in real time via a dedicated interface.
Anti virus
Your e-mails are scanned by 6 antivirus programs plus a high-performance suspicious file detection system to block known and unknown viruses. Our virus databases and detection engines are updated several times an hour, incorporating the latest developments.
Anti malware/ ransomware
Mailsafe blocks
ransomware
ransomware before it reaches your computer. mailboxes. Any malicious email or malware is filtered and stopped by our solution. The Mailsafe anti-malware and anti-ransomware solution blocks most sophisticated polymorphic malware and ransomware.
Anti phishing
Phishing is a counterfeit message presenting identity theft. It invites the recipient to reply or click on a link to provide information. The aim of this technique is to rob individuals of their login or bank details.
Anti spear phishing
Spear phishing is one of the most targeted and personalized of all email attacks. Spear phishing or BEC (Business Email Compromise) attacks are among the most costly attacks, based on the usurpation of the sender’s identity. Our Mailsafe email security solution is designed to detect president scams (
FOVI
) and spear phishing emails.
Anti-relay
Mailsafe from Altospam fights relaying to prevent your server being used by a third party to send illicit mail.
Anti scam
The
scams
are e-mail scams in which you are solicited for large sums of money.
Bounce management
Bounces are handled in such a way that legitimate bounces (those corresponding to real distribution failures concerning you) are accepted and those originating from spam sent by spammers who have impersonated you are refused. ALTOSPAM’s action on bounces can be configured to accept or reject them.
Denial of service (DDOS)
Your servers are no longer directly visible on the Internet, but are accessible via ALTOSPAM. Mailsafe includes specific rules to prevent denial-of-service attacks.
Anti advertising
Anti-advertising filtering is a free Mailsafe option for blocking the flow of advertising mails. Commercial email, unlike spam, is legal. Activating this option allows the administrator to block the reception of advertisements for some or all of his users.
How our anti-phishing, anti-spam, anti-ransomware solution works?
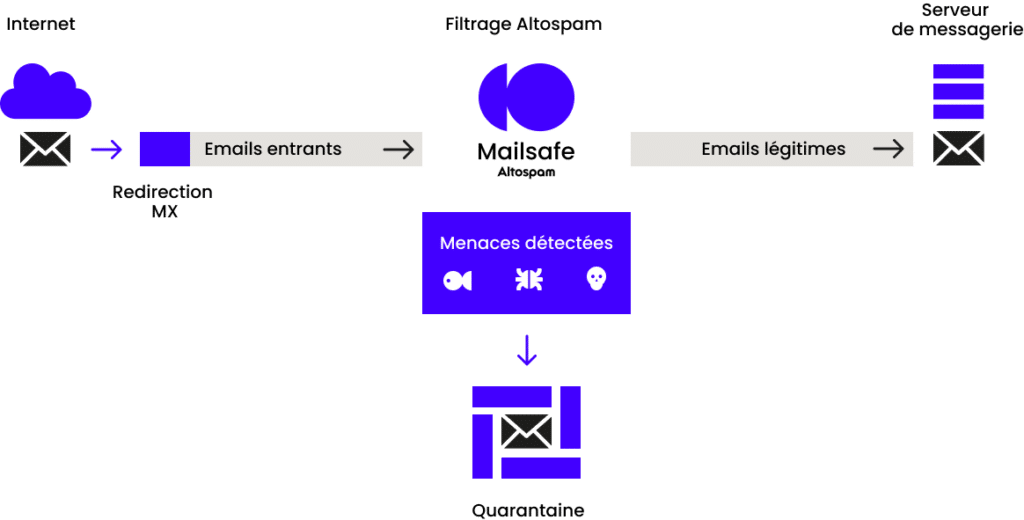
Altospam’s Mailsafe is a real-time online anti-spam and anti-virus solution. This service is an outsourced gateway through which all your e-mails pass to be sorted, filtered and redirected to your servers, or refused in the event of identified e-mail or malware: phishing, spear phishing, ransomware, spam or viruses. Your mail server then receives mail as before, but without spam or viruses.
You have access to your administration console, from which you can check whether spam or viruses have been detected. You can view your reports, analysis logs and manage your black and white lists.
If your mail server is unavailable for some time, your e-mails are temporarily stored on our ALTOSPAM servers until service is restored.
Altospam’s Mailsafe combines 16 anti-spam technologies, 6 anti-viruses and other security services such as anti-replay, anti-scam, anti-phishing, anti-advertising and protection against denial-of-service attacks (Ddos). Anti-ransomware systems combined with advanced anti-spam rules guarantee a veritable fortress against all types of known and unknown malware. What’s more, this e-mail security software ensures the highest possible availability of your e-mail.
Mailsafe’s strength lies in its judicious combination of the very latest techniques for detecting spam and cyber-attack threats: RBL, heuristics, Bayesian method, spam databases, URLs, DNS registration, automatic Whitelist, as well as the very latest Greylisting and Teergrubing processes.
Unsolicited e-mails and attack threats are rejected before they even reach your mail server, so they don’t clog up your network or your employees’ mailboxes, resulting in a quantifiable improvement in network performance. What’s more, this solution is synonymous with security, as it effectively combats phishing, spear phishing, ransomware, denial of service attacks, relaying and viruses.
Altospam’s commitment to quality guarantees a low rate of false positives (legitimate messages considered as spam), which can be detrimental to your business.
Based on a standard protocol, Altospam’s Mailsafe is compatible with your mail server. Our ASP (or SaaS) software is reasonably priced for both small businesses and international groups.
How Mailsafe anti-spam and anti-virus technology works
Heuristic analysis
Heuristic analysis is a set of rules represented as regular expressions. It searches for e-mails whose headers and/or bodies correspond to very specific characteristics known to have a high probability of being spam. ALTOSPAM uses a custom rules base to identify both American and French spam.
Blacklist | IP Reputation
RBL (Realtime Blackhole List) or DNSBL (Back List DNS) are lists of servers or networks known to assist, host, produce or retransmit spam, or provide a service that can be used as a medium for sending spam. Mailsafe uses the leading community and commercial RBLs on the market.
Collaborative spam databases
These spam signature databases are used in the same way as virus signature databases. They are fed by users of anti-spam solutions.
DNS records
Checks the correlation between the source server’s IP address and its name via a reverse DNS query. Typically, dedicated mail servers have a fixed, bijective IP address with its associated domain name. This information can’t always be used with shared messaging services, but is still worth including in the analysis.
Bayesian filters
Probabilistic filtering method learning e-mails based on the statistical distribution of keywords in e-mails. This type of algorithm adapts itself based on the analysis of known spam and non-spam emails.
White list
List of safe sites, hosts, domains or addresses. By default, very few hosts are considered safe, as their addresses could be spoofed by spammers. However, Altospam uses a self-learning whitelist system to speed up processing time for transmitters already tested and considered safe. What’s more, Altospam lets you set up your own whitelist.
Transaction history
Previous transactions between the sender and receiver of a message influence the result of the analysis. People who are used to sending each other legitimate e-mails have no reason to send each other spam.
URL addresses
The purpose of analyzing the URLs in the message body is to identify and filter the e-mail according to the desired action: the user clicking on a promotional link. This analysis is based on the detection of suspicious sites and URLs (numeric, badly formatted).
SPF and DKIM
Anti-spam techniques known as SPF (
Sender Policy Framework
) and DKIM (
DomainKeys Identified Mail
) are designed to authenticate the sender of a message. SPF announces the mail servers authorized to send emails for a given domain. DKIM signs emails sent by mail servers to ensure their integrity.
Sender domain validation
To be considered legitimate to send e-mail, a domain must comply with a certain number of standards. We analyze the email sender’s domain to validate that the sender is able to receive emails.
Image, HTML & Pdf analysis
HTML code embedded in messages, as well as certain PDF files, may contain dangerous javascript elements. Mailsafe examines the HTML code and PDF files contained in an e-mail to identify any dangerous code or abnormal behavior.
ALTOSPAM examines the images and PDF files contained in an e-mail on various bases: number, type, size, format and dimensions, then compares these criteria with the characteristics of the images used by spammers.
Teergrubing
A technique for significantly reducing the response speed of the server by maintaining the session.
SMTP, on certain connections considered suspicious. Teergrubing can be used to restrict the spam server.
Greylisting
The greylisting is an anti-spam technique that consists of temporarily rejecting a message, by sending a temporary refusal code to the sending server. The sending server resends the mail after a few minutes – most spam servers don’t bother! (Cf.
Our article on Greylisting)
Turing test
This technique, also known as challenge/response, consists of sending an email requesting authentication to the sender.
authentication request to the sender
of the message (via the reproduction of a displayed code) to ensure its actual physical existence. Used on its own, this technology has a number of disadvantages (filtering work shifted to the message sender, systematic sending of often unsolicited messages, generation of false positives). When integrated with other technologies and used judiciously at the end of the analysis, it frees up the
false positives unresolved.
Office document control
VBA macros or scripts in Office documents are currently one of the main vectors of viral infection. Using sandboxing, Mailsafe monitors the activity of these scripts to establish their potential dangerousness, in order to identify and block dangerous attachments.
How Mailsafe anti-spam and anti-virus technology works
SIMPLE
- Installation and set-up in 5 min
- Rapid deployment, turnkey solution
- Automatic learning of e-mail addresses.
- Real time: immediate results.
- No financial or human investment.
- Stand-alone operation, with built-in updates.
- Simple, comprehensive interface.
- Detailed statistics and reports
SAFE
- Protects your mail server from outside intruders spam, visit virus, visit scams, the phishing, attacks by phishing, spear phishing, ransomware, denial of service and the relaying.
- Sovereign solution: Not subject to the Patriot Act
- Zero Trust: all emails are analyzed
- Redundant servers located in France
- Disaster recovery plan (DRP) 7 days
- SLA: 99.99% guaranteed (100% availability since 2002)
EFFECTIVE
- Detection rate: 99.5
- False-positive rate: 0.01%.
- Sandboxing: complete analysis of attachments & files
- Urls analysis
- SPF, DKIM, DMARC analysis
- Reduced network and server traffic
- Possible ad blocking
- Responsive French customer support 24/7
Prêt ? Partez. Déployez Mailsafe en 5 min.

Une mise en service rapide. Une protection immédiate.
Mailsafe d’Altospam ne nécessite aucune modification d’architecture, aucun paramétrage et aucun téléchargement ou installation de logiciel sur les postes utilisateurs. Mailsafe d’Altospam s’intègre directement dans votre environnement informatique existant. Une simple modification d’entrée DNS est nécessaire pour que les emails soient envoyés sur les serveurs ALTOSPAM puis routés après analyse vers votre serveur de messagerie.
Mailsafe d’Altospam est bâti sur une architecture redondée qui lui confère une très haute disponibilité assurant ainsi une accessibilité permanente à votre messagerie. De plus, si votre serveur de messagerie est indisponible pendant un certain laps de temps, vos courriers électroniques seront stockés temporairement sur nos serveurs ALTOSPAM jusqu’au rétablissement du service.
Our technology combines analysis efficiency, performance and ease of administration.
Mailsafe in figures
Prêt ? Partez. Déployez Mailsafe en 5 min.
1. Mise en service immédiate : changez simplement le MX de votre messagerie
2. Apprentissage automatique de l’ensemble des adresses mails à protéger sur le domaine
3. Protection instantanée : accédez à vos rapports de statistiques en temps réel & découvrez les menaces d’intrusion stoppées
Ready? Go. Deploy Mailsafe in 5 min.
Votre Interface d’administration. Une interface paramétrable selon vos besoins avec un contrôle total pour l’administrateur.
L’interface de la solution SaaS Mailsafe est accessible directement en ligne. Elle vous permet de visualiser toutes les informations concernant les emails reçus sur vos domaines (statistiques, logs en temps réel, classement, configuration,…).
Mailsafe est une solution complète qui ne nécessite aucune configuration lors de son installation. Vous êtes en mesure de superviser votre flux d’e-mails, gérer les paramètres de sécurité et les droits des utilisateurs directement depuis votre interface. Vous avez une vue à la fois détaillée et synthétique des tentatives d’intrusions /d’attaques ainsi que de l’ensemble des mails et messages valides, suspects ou rejetés en temps réel.
En tant qu’administrateur, vous avez le contrôle de l’ensemble des paramètres de votre structure. Vous avez accès à une interface sécurisée qui vous permet de relâcher les emails placés en quarantaine et de gérer les listes blanches et noires Vous pouvez également configurer des rapports pour être informé en cas d’activités suspectes.

Une interface d’administration paramétrable selon vos besoins avec un contrôle total pour l’administrateur.
They protect their mailboxes with Mailsafe
They already trust us to protect their emails
-
How long does it take to set up Altospam's Mailsafe solution? Do I need to install software?
La solution Mailsafe d’Altospam est mise en place en quelques minutes après signature du contrat utilisateur et paiement. Sa mise en place nécessitant la modification de votre DNS, il convient de prévoir une durée de 48 heures, liée au rafraîchissement des DNS internationaux, pour être certain que tous les mails transitent bien par Mailsafe d’Altospam. Quel que soit le temps nécessaire aux rafraîchissements des DNS, tous les messages vous arriveront
-
How much spam is actually blocked by Altospam's Mailsafe?
Le taux mesuré sur notre plate-forme est actuellement de l’ordre de 98,7%. Vous pouvez considérer, suivant le risque d’exposition de votre société aux spams, qu’ALTOSPAM bloquera entre 99% et 100% des spams. D’autre part, Altospam s’engage contractuellement sur la qualité de service (SLA) en garantissant un faible taux de spams et de faux positifs, ces messages légitimes interprétés comme spams.
-
What exactly do you mean by false positives?
Un faux-positif est un message licite interprété par une solution antispam comme étant un spam. Le taux de faux-positifs est le critère le plus important de qualification d’une solution antispam. C’est pourquoi ALTOSPAM a été pensé dès sa conception de manière à réduire au maximum le taux de faux-positifs.
-
Does ALTOSPAM increase the delivery time of legal e-mails?
En règle générale, les messages arrivent aussi rapidement que d’habitude. Ils transitent par Mailsafe d’Altospam et sont immédiatement renvoyés sur le serveur de votre entreprise. Par contre, en cas d’ambiguïté sur la nature d’un message, ALTOSPAM peut générer un délai de l’ordre d’un quart d’heure à une demi-heure lié à l’utilisation de la technique avancée de Greylisting.
-
How can you be sure that an important email isn't mistakenly spammed using Altospam's Mailsafe solution?
Il s’agit là de toute la problématique des faux positifs. Le logiciel antispam et antivirus Mailsafe d’Altospam combat ce problème sur trois fronts:
1- en limitant au maximum le taux de faux positifs,
2- en assurant que, dans le cas de détection d’un mail comme faux positif, l’expéditeur soit informé que son mail n’est pas parvenu à son destinataire,
3- en vous permettant de visualiser l’historique des messages traités via l’interface d’administration ou via la réception quotidienne d’un mail de synthèse de vos logs afin d’identifier et de libérer d’éventuels faux positifs. -
What is the guaranteed availability of ALTOSPAM servers?
Chaque client ALTOSPAM dispose de plusieurs serveurs ALTOSPAM pour assurer une haute disponibilité en cas de problème sur un des serveurs. De plus, les serveurs ALTOSPAM sont situés sur des sites géographiques différents pour anticiper tout problème de connexion à Internet ou autre. Une garantie de disponibilité du service (SLA) est également intégrée dans nos contrats utilisateurs. Pour plus de détails, le flux Garanties et services Altospam présente certains de ces différents aspects.
-
What happens if my mail server is down for several hours?
Mailsafe d’Altospam assure une “bufferisation” de vos emails pendant 5 jours. Votre serveur peut donc rester indisponible pendant plus de 120 heures sans que cela ne pose de problème. Au-delà de ce délai, un message d’erreur est envoyé aux expéditeurs.
-
Why use an ASP outsourced solution like ALTOSPAM? Can we install Altospam's Mailsafe on our company's mail server?
L’intérêt est multiple: d’une part vous ne saturez ni votre connexion Internet ni votre serveur de messagerie avec des emails illicites, d’autre part vous ne vous préoccupez de rien : vous n’avez aucune installation et mise à jour à effectuer. La solution ALTOSPAM est proposée exclusivement en mode ASP, il n’est pas possible d’installer de serveurs antispam ALTOSPAM dans votre société.
-
Do I need a domain name?
OUI, la solution ne peut être mise en place que pour les structures possédant leur propre nom de domaine. Mailsafe d’Altospam propose en option d’enregistrer votre nom de domaine si vous n’en possédez pas.
-
How long is Altospam's Mailsafe service contract and can I opt out at any time?
Par défaut, la durée du contrat est de 1 an, renouvelé par tacite reconduction.
Le contrat peut cependant être rompu à tout moment par lettre recommandée en respectant un préavis de quinze jours. -
Is my company's use of Altospam's Mailsafe solution transparent to my email correspondents?
La solution anti-spam et anti-virus Mailsafe d’Altospam est complètement transparente pour l’expéditeur de messages dont vous êtes le destinataire. Les serveurs ALTOSPAM sont configurés comme serveurs de mails de votre société au niveau de votre DNS ; ils redirigeront ainsi les mails licites vers votre serveur de messagerie.
-
Altospam's Mailsafe is an outsourced solution, so where does my company's email go? How are the security and confidentiality of our e-mails guaranteed?
Tous les serveurs ALTOSPAM sont physiquement présents dans des datacentres français. Les serveurs sont hautement sécurisés de manière à garantir l’intégrité et la confidentialité de vos communications électroniques. De plus la confidentialité des messages est garantie contractuellement.
-
I use a mail server provided by an outsourced host. Can I still use Altospam?
Au même titre que si votre serveur était situé dans vos locaux, si votre serveur de messagerie est hébergé chez un tiers ou bien s’il s’agit d’un service mutualisé proposé par un hébergeur spécialisé, cela ne change rien, vous pouvez profiter du service antispam et antivirus ALTOSPAM.
-
What message analysis techniques does Altospam Mailsafe use?
ALTOSPAM est basé sur un procédé extrêmement perfectionné de notation des emails s’appuyant sur de multiples techniques d’analyse : RBL (listes noires), analyse heuristique, méthode bayésienne, bases de spams, vérification des URL, enregistrement DNS,… (Cf. liste des technologies anti-spam utilisées). Mais le plus important réside dans l’action réalisée suivant la notation du message : accepter, refuser temporairement (technique de Greylisting), rejeter de façon permanente l’email ou maintenir la session ( Teergrubing). Ces actions, notamment la technique duGreylisting, permettent d’accroître très significativement les résultats d’analyse.
-
What is Greylisting?
Le Greylisting consiste à refuser temporairement un message. Si l’émetteur est un véritable serveur de messagerie (càd spécifique à la RFCSMTP) le message sera forcément réémis puis accepté. Dans le cas contraire il sera rarement réexpédié. C’est la raison pour laquelle ALTOSPAM utilise cette technologie en cas d’ambiguïté sur la nature du message. En contrepartie cette technique génère un temps de latence dans la réception des emails (Cf. article sur le greylisting).
-
Why use a French solution?
La solution Mailsafe d’Altospam