Ransomware, your data held hostage. What is ransomware and how can I protect myself against it?
Definition of Ransomware
Ransomware is malicious computer software that takes data hostage. Ransomware encrypts and blocks files on your computer and demands a ransom in exchange for the key to decrypt them. Initially appearing in Russia, ransomware has spread to systems all over the world, particularly in the USA, Australia and Germany. Very often, ransomware infiltrates a computer in the form of a worm or malware, through a file downloaded or received by email, and encrypts the victim’s data and files. The aim is to extort a sum of money. They will most often demand payment in virtual currency (bitcoin) to avoid any trace. Ransomware is currently one of the main threats to all computer systems connected to the web.
Example
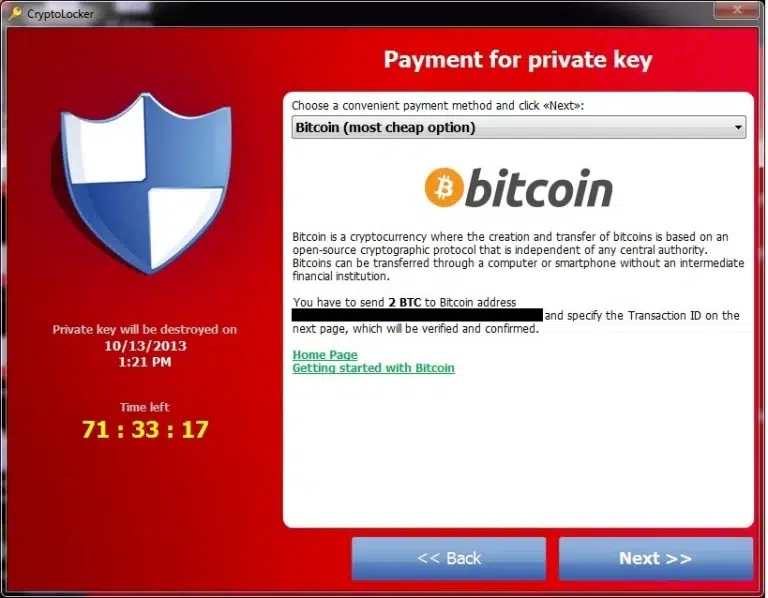
All the files on your computer are quickly encrypted. A message appears informing you that you must pay to recover your data. Known ransomware names: CryptoLocker, CryptoWall, Reveton, …
How to protect yourself against ransomware attacks?
To counter ransomware, Altospam automatically targets and detects dangerous files, using 6 anti-virus scanners and 4 additional scanning stages that deconstruct attachments and detect unknown viruses (more details).
Business users can protect themselves against ransomware for just a few euros a month. Messaging protection is just as much a must-have as antivirus software. Protect your company effectively from ransomware attacks in just a few minutes by using an email protection solution. 80% of malware and viruses are introduced into computers, the cloud and corporate networks by software hidden in a file received in an email, particularly Microsoft Office documents, containing macros or VBA scripts.
Users can receive this type of attack via one of their trusted contacts, who has been hacked by cybercriminals. It’s important not only to protect incoming emails, but also to secure outgoing ones, so as not to be held responsible for an attack originating from your company. Employees can unwittingly spread ransomware when their mailbox or computer is hacked. Companies, and especially IT departments, need to anticipate these threats to avoid falling victim to malware and other malicious software.
What should you do if you fall victim to ransomware?
If you are the victim of a ransomware attack, your computer system is probably blocked and your data is probably encrypted. Ransomware can spread via the cloud, the internal network or the Internet. You need to disconnect all your computers and backup disks to prevent the encryption from spreading.
- The first thing to do is not to switch off your computer, but to isolate it from your network or cloud and disconnect it from the Internet: to do this, simply unplug the network socket to interrupt all connections and isolate the ransomware from other clients. Then alert your IT service provider, who manages your network and security, as well as all your company’s users.
- Paying the ransom is not recommended, as cybercriminals will not necessarily give you the decryption key. All you’ll be doing is feeding the system and convincing the hacker to continue what he’s doing.
- It is vital to report any attacks to the authorities specialising in cyber security and to lodge a complaint. Investigators will need access to the infected machines and customers, and will be able to help you if the encryption is known to the security services. By preserving these elements, it is possible to characterise the software used in the ransomware and identify the source of the attacks so that they can be countered more effectively. In some cases, it is possible to decrypt the encryption, but to do this you need to recover as much information as possible about the attack. Off-site back-ups, disconnected from the company network, are an additional security measure to overcome this type of IT threat.
- The next step is to identify the source of the infection to prevent it spreading again. Carry out an in-depth scan of all devices and computers using dedicated cybersecurity tools such as antivirus software that you have updated beforehand.
Once all your IT equipment has been secured and the breach identified, you can re-establish your connection and networks, and reinstall your software and backup files.
Why should you protect yourself against ransomware?
In 2022, Clestra (€145m turnover, 700 employees) was placed in receivership after falling victim to a ransomware attack. After 7 weeks of complete shutdown, at a cost to the company of between €2 and €3 million, it was able to resume business.
Many hospitals have also recently fallen victim to ransomware attacks, blocking the management of critical medical services.
The consequences of a ransomware attack can be tragic, and are becoming increasingly common with mafia-style networks of cybercriminals. Whether you use a Mac or a Microsoft Windows PC, the problem is the same. Different types of machines and operating systems do not protect against ransomware-type threats.
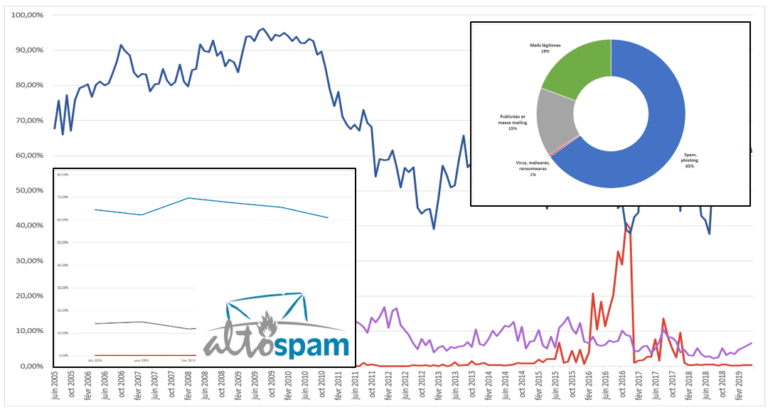
Ransomware: figures and statistics
Application
Ransomware, although present in less than 0.5% of emails, is potentially very dangerous. A single virus can compromise a company’s entire operation, which is why we are committed to doing everything we can to block it and to building a veritable fortress against all viruses and malware. That’s why Altospam’s Mailsafe includes 6 complementary antivirus and unknown virus detection systems. All emails and their attachments are systematically scanned by these six antivirus programs.

1 in 2 businesses was attacked in 2022
We help companies protect themselves against external phishing attacks, ransomware, spear phishing… We offer a free analysis of attempted intrusions into your email system for 15 days.