Botnets and networks of zombie computers
Definition of botnet
A botnet is a network of computers compromised and remotely controlled by hackers for malicious purposes. These computers are often infected with malware such as Trojans or viruses, and are used to carry out Distributed Denial of Service (DDoS) attacks, spread spam or malware, or steal personal information.
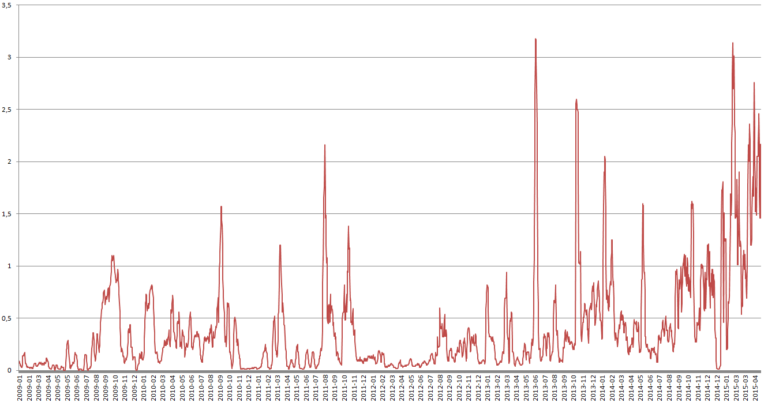
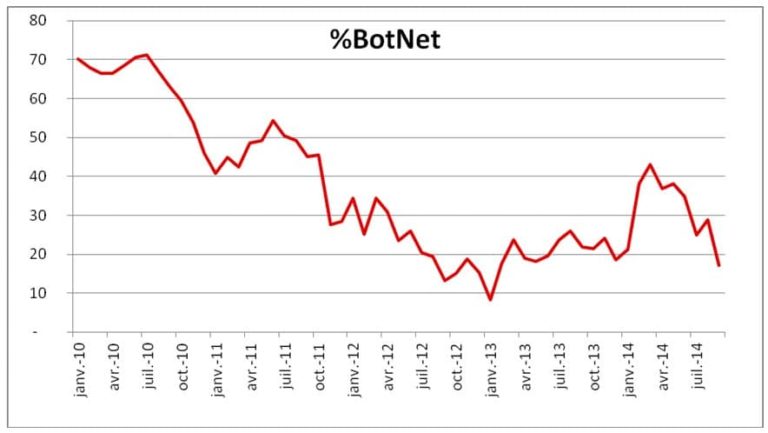
A botnet is a network of zombie machines (computers infested with a trojan and controlled without their knowledge) connected to the Internet. The botnet is remotely and globally controlled by a botmaster to perform often repetitive tasks on a large scale. The botmaster hides his identity via proxies, the TOR network and/or shells to mask his IP address.
The term was originally used to designate the early IRC bots responsible for managing chat channels or running various useful services. It now refers to these zombie machines used for malicious purposes such as sending spam, viruses, ddos attacks, bruteforcing attacks or large-scale bank fraud operations.
There are two main methods of infection for creating a zombie and adding it to a botnet: drive-by downloads and infected e-mails. In the first case, you end up with a malicious program on your PC without realizing it, after visiting an infected site or downloading a rogue application. In the second case, the program infiltrates our PC by opening an infected link or attachment, and ends up in the botnet.
How do botnets work?
Botnets work by installing malware on compromised computers using techniques such as phishing. Infected computers are then remotely controlled by hackers, who can use them to launch attacks or gather information. Hackers can send instructions to infected computers to launch attacks or collect information.
How can I protect myself from botnets?
To protect yourself from botnets, it’s important to keep security software and operating systems up to date, not to click on suspicious links or attachments, and to use security software like Altospam’s Mailsafe to detect and remove malware. It’s also important to limit computer access to the Internet, and to set up security policies for users.
How to detect a botnet?
Botnets can be detected using security software that can identify suspicious activity on computers, such as outgoing connections to unknown IP addresses or communication with command and control servers. Abnormal behavior, such as high bandwidth usage or increased network traffic, can also be signs of botnet infection.
Applications with Altospam’s Mailsafe solution
In the context of spam and virus prevention, botnets are detected either by direct analysis of the smtp transaction originating from a non-fqdn user workstation, or by the standard antispam and antivirus analysis technologies integrated into Altospam Mailsafe. Trojans designed to create botnets are blocked in the same way as viruses and ransomware, via the anti-malware fortress.
Phishing, Ransomware, spams ?
Security starts in your mailbox. We offer a free 15-day e-mail analysis.