How do attackers target their victims in a spear phishing attack?
Attackers may target their victims by gathering information from public sources, social networks or other data available online. They may also send emails to people in key positions within an organisation, such as senior executives or IT managers, to increase the chances of a successful attack.
What are the warning signs of a spear phishing attack?
Warning signs of a spear phishing attack can include emails that seem too good to be true, grammatical errors or spelling mistakes, unusual requests for personal or financial information, suspicious email addresses or links, or an artificial urgency created to prompt quick action.
How can I protect myself against spear phishing?
To protect yourself against spear phishing, we recommend that you :
- Be vigilant and check the legitimacy of e-mails you receive.
- Do not click on links or download attachments from suspicious e-mails.
- Use security tools such as spam filters and anti-virus software.
- Regularly update software and operating systems to plug vulnerabilities.
- Train employees to recognise spear phishing attacks and adopt online security practices.
What techniques are commonly used in spear phishing attacks?
Spear phishing attacks can use techniques such as impersonating a known person or organisation, creating fake websites or forms to collect information, using malicious links or infected attachments, or exploiting news events to incite action.
What are the risks and consequences of spear phishing for individuals and organisations?
The risks and consequences of spear phishing can be serious for individuals and organisations. Individuals can fall victim to identity theft, theft of personal or financial information, or even financial fraud. For organisations, spear phishing can lead to data breaches, financial losses, reputational damage and business disruption.
How can I spot and report a spear phishing e-mail?
To spot a spear phishing e-mail, you can look out for signs such as unusual requests for information, grammatical or spelling errors, suspicious e-mail addresses or links to dubious websites. It is important to check the authenticity of the sender and not to click on links or download attachments from suspicious e-mails. If you identify a spear phishing email, report it to your IT security team or system administrator.
How can companies strengthen their security against spear phishing?
To strengthen their security against spear phishing, companies can take the following steps:
- Set up anti-spam and anti-phishing filters to block suspicious e-mails.
- Use advanced threat protection solutions to detect spear phishing attacks.
- Regularly update software and operating systems to plug vulnerabilities.
- Implement e-mail authentication, such as SPF, DKIM and DMARC, to verify the authenticity of messages.
- Regularly train employees on email security and best practices for detecting spear phishing.
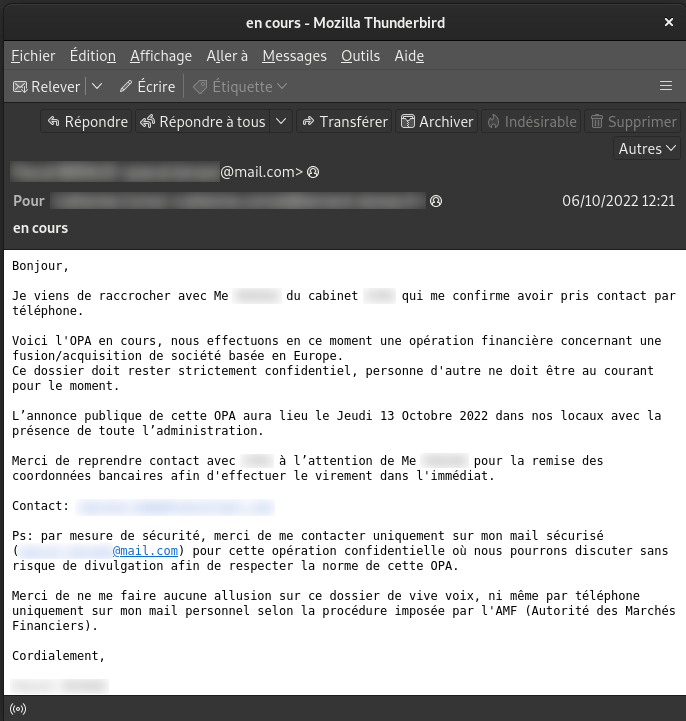
Example of a spear phishing email