Securing SMTP flows with StartTLS
Definition of StartTLS
Traditionally, secure and non-secure communications take place on different ports, as in the case of Web browsing (HTTP on port 80 and HTTPS on port 443). This architecture poses a number of problems (see section 7 of RFC 2595).
StartTLS (or opportunistic TLS) enables an unsecured connection to be elevated to a secure connection on a single port: in a first clear exchange, client and server communicate about their respective encryption capabilities and agree to establish this secure channel, after which the rest of the communication is encrypted. If no compatible encryption method is found, communication can continue in clear text. It is therefore an interoperability solution that enables a maximum number of disparate devices to communicate under the best possible conditions.
The protocol does, however, have its limits, and the first, unsecured phase is susceptible to interception and even modification. Complementary systems, such as DANE, have therefore been put in place to close the loopholes in StartTLS.
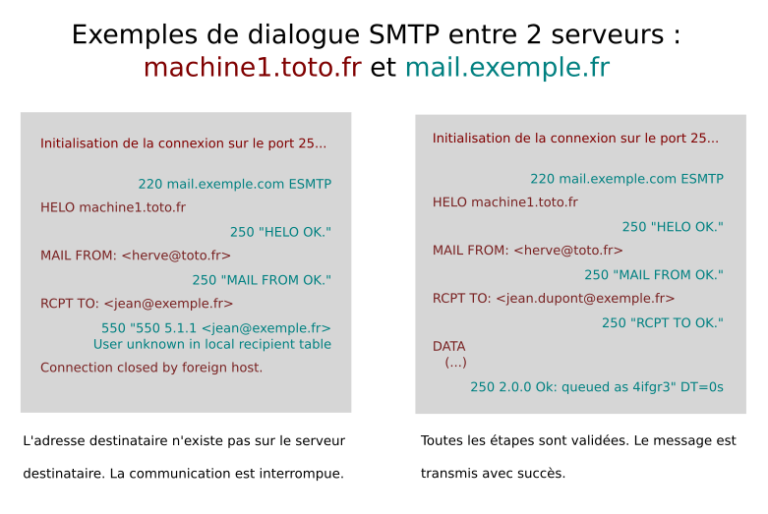
Examples
Here’s the representation of an SMTP communication using StartTLS between a sending server “mail.envoi.fr” (in blue below) and a receiving server “mail.dest.fr” (in green):
1 → Establishing the connection from mail.envoi.fr to mail.dest.fr over TCP/25.
2 ← 220 mail.dest.fr ESMTP (recipient presents itself).
3 → EHLO mail.envoi.fr (sender introduces himself)
4 ← 250-(…) 250-STARTTLS (the recipient transmits its parameters, including its StartTLS capability)
5 → STARTTLS (sender requests to use StartTLS)
6 ← 220 Go ahead (recipient confirms TLS connection)
7 → Client Hello (sender initiates secure connection, stream is now encrypted)
8 ← Server Hello, Change Cipher Spec (recipient confirms and proposes several algorithms)
9 → Change Cipher Spec (the sender selects his preferred algorithm and validates the change)
10 ← ACK (recipient confirms change)
11 → EHLO mail.envoi.fr (resumption of SMTP communication, now encrypted)
In this example, steps 1 to 6 are unencrypted. In step 7, the sender initiates encrypted communication using the compatible protocol defined in step 5. Depending on the configuration, the client or server defines the best algorithm to use. Secure communication finally resumes at step 11, with the data being exchanged.
Applications :
StartTLS is protocol-dependent. As we saw in the previous example, it is during SMTP communication that a parameter is issued to indicate that StartTLS is available. Only a few protocols have integrated StartTLS: IMAP, POP3, SMTP, XMPP and NNTP. At our level, StartTLS is used for SMTP communication in all cases, provided the other party’s server is compatible. Altospam servers are configured to select the encryption algorithm used (Cipher preference), automatically choosing the strongest compatible encryption algorithm.
Email is the main vector for cyberattacks
New and increasingly sophisticated attacks are being launched around the world every day. Our solution detects and neutralizes phishing, spear-phishing, malware, ransomware and spam threats in real time.