DMARC: Domain-based Message Authentication, Reporting and Conformance
Definition of DMARC
DMARC is a technique for protecting against email fraud using authentication protocols such as SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail). It enables domain owners to specify actions to be taken for emails that do not comply with their authentication policy, such as unsigned or invalid emails.
Domain-based Message Authentication, Reporting and Conformance (DMARC) is a standard for preventing your domain from being spoofed to send e-mail. It uses the DKIM (DomainKeys Identified Mail) and SPF (Sender Policy Framework) mechanisms and gives instructions to the server receiving the e-mails if at least one of the two protocols is not respected. To implement the DMARC policy for your domain, you’ll need to add a new TXT entry in the DNS zone.
What is a DMARC record?
A DMARC record is an entry in a domain’s DNS zone, containing instructions for mail servers on how to handle messages that do not comply with the sender’s policy. It contains information on SPF and DKIM authentication policies, as well as contact email addresses for DMARC reports.
How do I set up DMARC?
To set up DMARC, start by creating a DMARC record in the domain’s DNS zone. This record specifies the DMARC policy and the e-mail addresses to which DMARC reports should be sent. Next, domain owners must configure the SPF and DKIM protocols to sign and authenticate outgoing emails. Finally, they need to monitor DMARC reports for any suspicious activity.
How do I read a DMARC report?
DMARC reports are sent to the contact email addresses specified in the DMARC record. They contain information on outgoing e-mails that have failed SPF and DKIM authentication, as well as the IP addresses of the servers that sent these messages. Domain owners can use these reports to identify potential sources of email fraud and adjust their security policies accordingly. DMARC reports can be read using specific visualization tools, such as DMARC report analysis tools.
Examples
There are a number of simple examples of use for concrete cases. In concrete terms, this involves adding a TXT field named “_dmarc” directly under your domain (for example: “_dmarc.altospam.com.”).
If you want all emails to be blocked when they don’t comply with DKIM and SPF rules, in this case you’ll opt for the following configuration:
“v=DMARC1; p=reject;”
Now you’d prefer emails to be quarantined on the recipient’s premises if they don’t comply with DKIM and SPF procedures. You’ll configure DMARC as follows:
“v=DMARC1; p=quarantine;”
It’s perfectly possible to take no action at all, but to send a report to the domain owner with the following example:
“v=DMARC1; p=none; rua=mailto:adresse_email@votre_domaine.fr”
There are a large number of options, here are the main ones:
“v=DMARC1; p=quarantine; pct=100; rua=mailto:email@example.org; adkim=s; aspf=r; ri=86400”
v: Dmarc version.
p: Policy to be applied to the domain (and subdomain by default) when a mail does not comply with DKIM and SPF rules. The value can be quarantine|reject|none. In the example, mails that don’t comply with DKIM and SPF rules will go to junk mail.
pct: Percentage of filtered mails.
rua: e-mail address to which the daily global report is sent.
ri: time in seconds between the sending of 2 reports.
aspf: indicates whether the SPF test should be strictly (s) or moderately (r) applied.
adkim: indicates whether the DKIM test should be strictly (s) or moderately (r) applied.
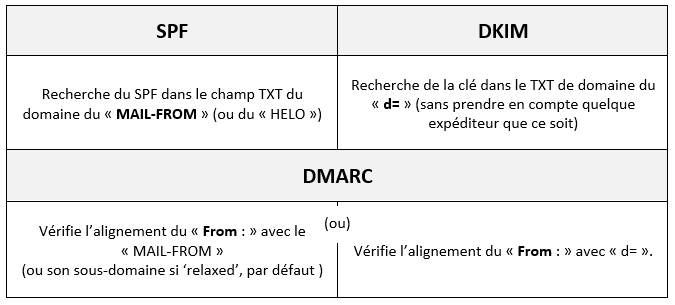
DMARC alignment: DMARC checks that the “From:” of the message corresponds to the “MAIL FROM” used by SPF and/or the domain entered on DKIM. To understand the difference between “From:” and “MAIL FROM”, please consult this article. The summary below will help you understand DMARC alignment.
Altospam applications
DMARC-compliant emails are less likely to be considered spam, which is good for the deliverability of your emails. We recommend configuring DMARC both when using Altospam’s MailOut and Mailsafe services.
Would you like to strengthen your organization’s security?
Security starts in your mailboxes. We offer a free 15-day analysis of your inbox.


